How Ransomware Attacks Your Business
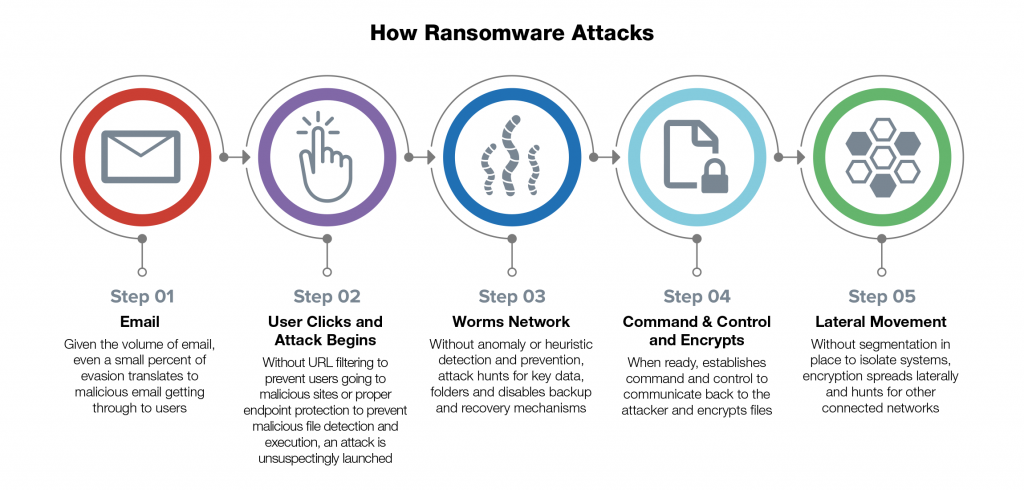
How Ransomware Gets In
The pressing need for speed and agility across business’s of all sizes has led to the rapid adoption of innovations (e.g., cloud-based tools, Software-as-a-Service [Saas], smart devices) that bring convenience along with complexity—quickly creating vulnerabilities and making it easier for even basic threats to get past outdated defenses at various points of entry.
Ransomware-as-a-Service (RaaS) that enables attackers to merely invest in an attack carried out by others and the natural IT knowledge of younger generations have made it easier for low-level hackers to easily blast a wide target base and expose one of those holes and is one reason that has led to such high rates of SMBs being hit with ransomware.
Email Vulnerabilities
Email is the primary way that ransomware gets inside a business’s network. Many users still unintentionally open a malicious attachment or URL that slips by consumer-grade email filters. More often these days, attackers rely on social engineering and business email compromise (BEC) scams where users unknowingly give attackers the information they seek to set off a series of events—like getting the victim’s phone number and replicating known sites to obtain user credentials. For SMBs that often rely on consumer-based email solutions that lack advanced email security checks, recognizing threats and avoiding social engineering schemes rely on a user’s individual judgment to identify the threat and avoid infection.
Exposed Ports and Default or Weak Passwords
With so much to do and the security implications of new technologies not being fully understood before implementation, it is common for organizations to simply forget or be unaware of potential security holes. Remote Desktop Protocol (RDP) is often used as an initial entry point for attackers. RDP is used by IT staff to troubleshoot problems with an employee’s device via remote control, but that same remote access can be exploited by attackers without the proper protections in place. By detecting public-facing ports, attackers can use brute-force tactics and stolen credentials to gain entry into an organization’s systems and ultimately inject their malware. For SMBs, this is even more of a risk as they adopt new technologies (such as smart devices and cloud-based applications) without dedicated staff resources and tools to ensure proper visibility and control of everything on the network.
Malicious URLs
Accidentally going to a website that has been hacked or that has been falsely replicated offers attackers a variety of tactics to infect unknowing users. They can scan the user’s machine for application vulnerabilities and inject code directly via drive-by download, or they can capture credentials and other information for later use. Hackers are able to control these sites by exploiting application vulnerabilities in the website itself and copy the look, feel, and interaction—otherwise known as “spoofing” the site. Users believe they are inputting information into a valid site interface while unsuspectingly sending information straight to their attackers. Often, users accidentally end up on these sites through mobile devices that are used for both work and personal use—clicking on links embedded in social media and unknowingly exposing themselves and their organization at the same time.
Challenges with Resetting to a Point Before the Attack
Perhaps the most common way of dealing with a ransomware attack is acknowledging that—despite best efforts—attackers have the advantage. Thanks to business system integrations, the smallest hole in outdated security defenses (ones that lack effective network segmentation controls inside the network) can result in an organizationwide infection.
The only remedy to an effective ransomware attack, other than making the payoff and hoping to receive decryption codes, is to restore the business’s systems to a state prior to the attack. However, a number of factors should be checked:
- When was the last time backup and recovery was tested to ensure it worked as planned?
- Have new systems and information been added to the backup process and tested accordingly?
- How long does it take to restore information and is this an affordable delay?
Despite these checks, restoring back to a prior “safe point” does not fix how the attack was initially successful. Also, if users have file synchronization turned on, encrypted files are automatically copied to SaaS clouds, and more advanced ransomware (such as the recent SamSam and Ryuk attacks) makes a point to delete shadow volumes and backup files—even in the cloud—to prevent recovery efforts.
Was It Only Ransomware?
If ransomware was introduced into the network, then attackers gained access. While ransomware may have been the primary motive, other nefarious tools—such as monitoring software, command-and-control (C&C) code, or assimilation into botnets—may have also been introduced to launch additional attacks or siphon data at a later date. Therefore, any ransomware-compromised business must do further investigation into logs and systems for full and effective remediation.
For more information on ransomware attacks and how KALM Services can keep you safe, or to schedule a technology assessment, Contact Us.
